[ad_1]
Stories from the SOC is a weblog sequence that describes latest real-world safety incident investigations performed and reported by the AT&T SOC analyst crew for AT&T Managed Extended Detection and Response clients.
Executive abstract
Humans are thought of the weakest hyperlink in cybersecurity. No matter how a lot an organization invests in firewalls, antivirus, and different safety software program to detect, deter, and forestall assaults people will all the time be the principle vectors for compromise. If no sufficient user-security coaching is supplied inside the group, they may all the time be in danger. Phishing is likely one of the oldest cyber-attacks but probably the most utilized by attackers as a consequence of its effectiveness and low price.
The Managed Extended Detection and Response (MXDR) crew acquired an alarm indicating a consumer had efficiently logged in from a rustic exterior of the United States (US. Upon additional evaluation, this was the primary time the consumer had logged in from exterior of the US. The analyst crew created an investigation by which the client responded and took the mandatory steps to get well the account from the attacker.
Investigation
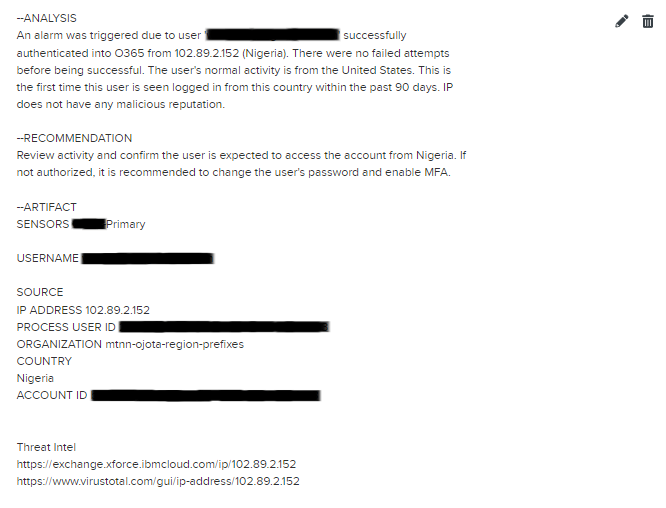
Initial alarm evaluation
Indicators of Compromise (IOC)
The preliminary alarm was triggered on account of the account being accessed from exterior of the United States. Due to the latest shift of distant working, it’s common to see customers accessing their accounts from completely different nations that may very well be attributable to Virtual Private Network (VPN) or due to journey exercise.
Expanded investigation
Events search
When investigating doubtlessly malicious habits, it is very important perceive what the baseline of a consumer’s exercise appears like. While trying on the historic knowledge for his or her exercise, logs confirmed this was the primary occasion the account has been accessed from exterior of the United States.
The logs didn’t present any failed login makes an attempt from one other nation, which is often seen each time an attacker makes an attempt to compromise an account.
Response
Building the investigation
After gathering sufficient data, an investigation was created for the client to verify if this must be anticipated from this consumer.
Customer interplay
Within minutes of the investigation being created, the client confirmed the consumer had clicked a phishing e-mail and enter their credentials, which the attacker then used to efficiently logged in into their account.
The phishing e-mail contained a URL to the next web site:
Once clicked, this web site would ship the consumer to a web page that impersonated a login for an e-mail account that was used to reap credentials.
Limitations and alternatives
Limitations
For this investigation, the MXDR crew didn’t have full visibility into the Microsoft Office 365 Exchange surroundings, hindering visibility into the preliminary assault. We have been unable capable of see the phishing e-mail being despatched to this account. The solely occasions being noticed by the SOC have been the profitable log ins from exterior of the United States.