[ad_1]
A infamous superior persistent risk actor generally known as Mustang Panda has been linked to a spate of spear-phishing assaults concentrating on authorities, schooling, and analysis sectors the world over.
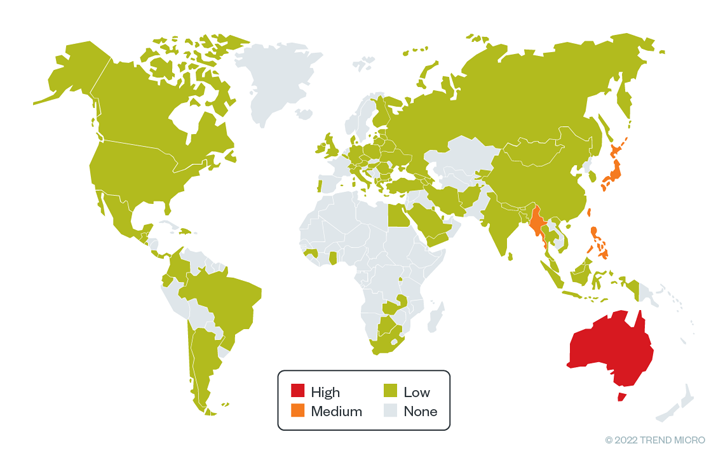
The major targets of the intrusions from May to October 2022 included counties within the Asia Pacific area reminiscent of Myanmar, Australia, the Philippines, Japan, and Taiwan, cybersecurity agency Trend Micro stated in a Friday report.
Mustang Panda, additionally referred to as Bronze President, Earth Preta, HoneyMyte, and Red Lich, is a China-based espionage actor believed to be lively since at the least July 2018. The group is understood for its use of malware reminiscent of China Chopper and PlugX to gather knowledge from compromised environments.
Activities of the group chronicled by ESET, Google, Proofpoint, Cisco Talos, and Secureworks this 12 months have revealed the risk actor’s sample of utilizing PlugX (and its variant referred to as Hodur) to contaminate a variety of entities in Asia, Europe, the Middle East, and the Americas.
The newest findings from Trend Micro present that Mustang Panda continues to evolve its ways in a technique to evade detection and undertake an infection routines that result in the deployment of bespoke malware households like TONEINS, TONESHELL, and PUBLOAD.
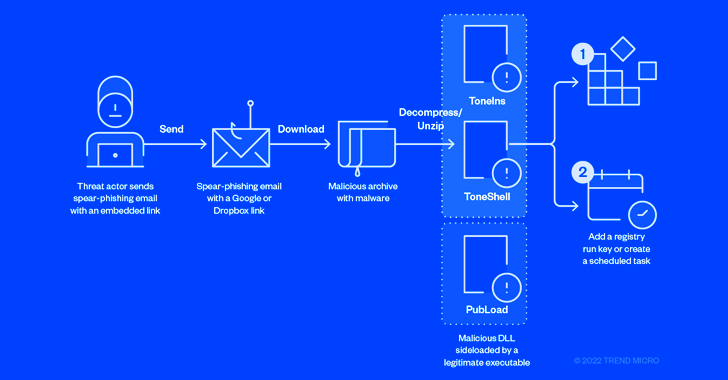
“Earth Preta abused faux Google accounts to distribute the malware through spear-phishing emails, initially saved in an archive file (reminiscent of RAR/ZIP/JAR) and distributed by Google Drive hyperlinks,” researchers Nick Dai, Vickie Su, and Sunny Lu stated.
Initial entry is facilitated by decoy paperwork that cowl controversial geopolitical themes to entice the focused organizations into downloading and triggering the malware.
In some instances, the phishing messages had been despatched from beforehand compromised e-mail accounts belonging to particular entities, indicating the efforts undertaken by the Mustang Panda actor to extend the chance of the success of its campaigns.
The archive recordsdata, when opened, are designed to show a lure doc to the sufferer, whereas stealthily loading the malware within the background by a technique known as DLL side-loading.
The assault chains in the end result in the supply of three malware households – PUBLOAD, TONEINS, and TONESHELL – that are able to downloading next-stage payloads and flying below the radar.
TONESHELL, the principle backdoor used within the assaults, is put in by TONEINS and is a shellcode loader, with an early model of the implant detected in September 2021, suggesting continued efforts on a part of the risk actor to replace its arsenal.
“Earth Preta is a cyber espionage group identified to develop their very own loaders together with present instruments like PlugX and Cobalt Strike for compromise,” the researchers concluded.
“Once the group has infiltrated a focused sufferer’s methods, the delicate paperwork stolen may be abused because the entry vectors for the subsequent wave of intrusions. This technique largely broadens the affected scope within the area concerned.”
[ad_2]