[ad_1]

A beforehand unknown ‘ARCrypter’ ransomware that compromised key organizations in Latin America is now increasing its assaults worldwide.
Threat actors behind the brand new ransomware household attacked a authorities company in Chile final August, focusing on each Linux and Windows methods and appending the “.crypt” extension on encrypted information.
Back then, Chilean risk analyst Germán Fernández advised BleepingComputer that the pressure appeared solely new, not related to any recognized ransomware households.
Researchers at BlackBerry have confirmed this by way of a report that identifies the household as ARCrypter and hyperlinks it to a second assault towards the Colombia National Food and Drug Surveillance Institute (Invima) in October.
BlackBerry additionally warns that ARCrypter is now increasing its operations exterior Latin America and focusing on varied organizations worldwide, together with China and Canada.
BleepingComputer confirmed this enlargement, additionally seeing ARCrypter victims in Germany, USA, and France.
The ransom calls for range and get as little as $5,000 in some circumstances seen by BleepingComputer, so ARCrypter operates as a mid-tier ransomware actor.
ARCrypter particulars
BlackBerry says the primary samples of ARCrypter appeared in early August 2022, just a few weeks earlier than the Chile assault.
The assault vector stays unknown, however the analysts had been in a position to find two AnonFiles URLs which can be used as distant sources for fetching a “win.zip” archive containing “win.exe.”
The executable is a dropper file that incorporates the sources BIN and HTML. HTML holds the ransom word information, whereas BIN incorporates encrypted information that requires a password.
.png)
If a password is offered, BIN will create a random listing on the compromised machine to retailer the second-stage payload, which is called utilizing random alphanumeric characters.
“While we were unable to identify the correct decryption key used for decryption of the BIN resource, we believe with a high degree of certainty that the second payload is the ARCrypter ransomware,” says BlackBerry within the report.
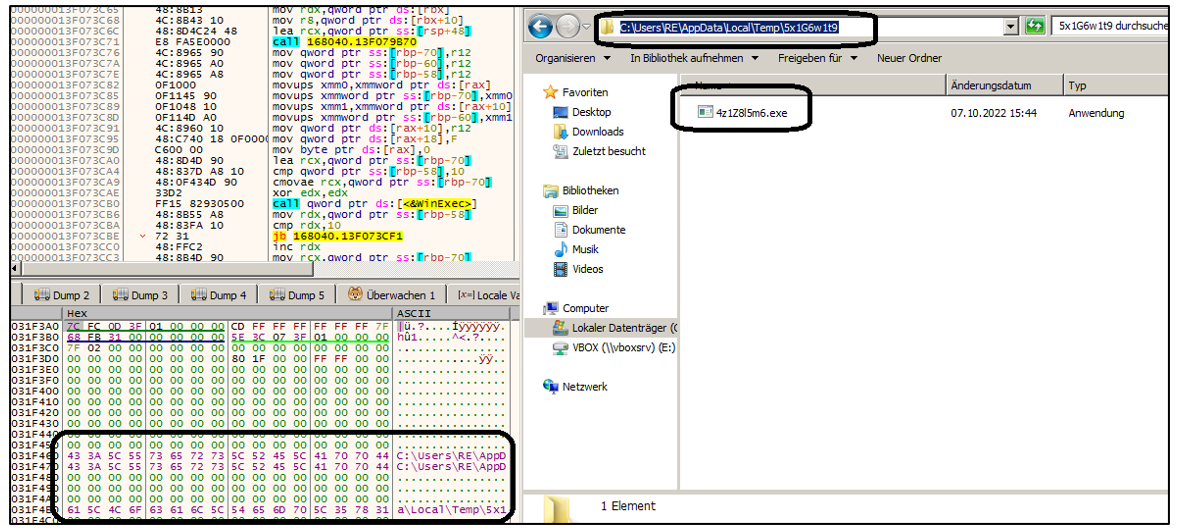
The ARCrypter payload then creates persistence by including the next registry key:
“HKLMSoftwareMicrosoftWindowsCurrentVersionRunSecurityUpdate”
Next, the malware deletes all Shadow Volume Copies to forestall straightforward information restoration, modifies community settings to safe secure connectivity, after which encrypts all information aside from the categories proven under.
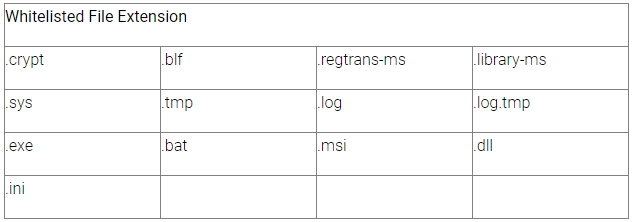
Files in crucial areas like “Boot” and “Windows” folders are additionally skipped to keep away from rendering the system fully unusable.
Apart from the ‘.crypt’ extension, encrypted information will present an ‘ALL YOUR FILES HAS BEEN ENCRYPTED’ message on the file supervisor, due to modifications to the next Registry keys:
HKCUControl PanelInternationalsShortDate
HKLMSYSTEMControlSet001ControlCommonGlobUserSettingsControl PanelInternationalsShortDate.png)
While the risk actors declare to steal information throughout their assaults, the ransomware operation doesn’t at the moment have a knowledge leak website that they use to publish information for unpaid victims.
At this time, little is understood concerning the operators of ARCrypter, their origin, language, and potential hyperlinks to different ransomware gangs.
