[ad_1]
Cybersecurity researchers have unearthed new samples of malware referred to as RapperBot which are getting used to construct a botnet able to launching Distributed Denial of Service (DDoS) assaults in opposition to sport servers.
“In truth, it seems that this marketing campaign is much less like RapperBot than an older marketing campaign that appeared in February after which mysteriously disappeared in the course of April,” Fortinet FortiGuard Labs researchers Joie Salvio and Roy Tay mentioned in a Tuesday report.
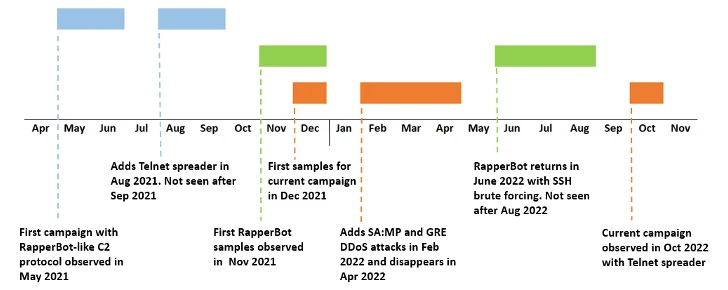
RapperBot, which was first documented by the community safety agency in August 2022, is thought to completely brute-force SSH servers configured to simply accept password authentication.
The nascent malware is closely impressed by the Mirai botnet, whose supply code leaked in October 2016, resulting in the rise of a number of variants.
What’s notable concerning the up to date model of RapperBot is its capability to carry out Telnet brute-force, along with supporting DoS assaults utilizing the Generic Routing Encapsulation (GRE) tunneling protocol in addition to UDP floods focusing on sport servers operating Grand Theft Auto: San Andreas.
“The Telnet brute-forcing code is designed primarily for self-propagation and resembles the outdated Mirai Satori botnet,” the researchers mentioned.
This checklist of hard-coded plaintext credentials, that are default credentials related to IoT gadgets, are embedded into the binary versus retrieving it from a command-and-control (C2) server, a conduct that was noticed in artifacts detected after July 2022.
A profitable break-in is adopted by reporting the credentials used again to the C2 server and putting in the RapperBot payload on the hacked machine.
Fortinet mentioned the malware is designed to solely goal home equipment that run on ARM, MIPS, PowerPC, SH4, and SPARC architectures, and halt its self-propagation mechanism ought to they be operating on Intel chipsets.
What’s extra, the October 2022 marketing campaign has been discovered to share overlaps with different operations involving the malware way back to May 2021, with the Telnet spreader module making its first look in August 2021, solely to be eliminated in later samples and reintroduced final month.
“Based on the plain similarities between this new marketing campaign and the beforehand reported RapperBot marketing campaign, it’s extremely doubtless that they’re being operated by a single risk actor or by totally different risk actors with entry to a privately-shared base supply code,” the researchers concluded.