[ad_1]

North Korean hackers are utilizing a brand new model of the DTrack backdoor to assault organizations in Europe and Latin America.
DTrack is a modular backdoor that includes a keylogger, a screenshot snapper, a browser historical past retriever, a working processes snooper, an IP deal with and community connection data snatcher, and extra.
Apart from spying, it may possibly additionally run instructions to carry out file operations, fetch further payloads, steal information and information, and execute processes on the compromised system.
The new malware model would not characteristic many purposeful or code adjustments in comparison with samples analyzed up to now, however it’s now deployed much more broadly.
A wider distribution
As Kaspersky explains in a report revealed right this moment, their telemetry reveals DTrack exercise in Germany, Brazil, India, Italy, Mexico, Switzerland, Saudi Arabia, Turkey, and the United States.
The focused sectors embody authorities analysis facilities, coverage institutes, chemical producers, IT service suppliers, telecommunication suppliers, utility service suppliers, and schooling.
In the brand new marketing campaign, Kaspersky has seen DTrack distributed utilizing filenames generally related to reliable executables.
For instance, one pattern they shared is distributed below the ‘NvContainer.exe’ file identify, which is similar identify as a reliable NVIDIA file.
Kaspersky informed BleepingComputer that DTrack continues to be put in by breaching networks utilizing stolen credentials or exploiting Internet-exposed servers, as seen in earlier campaigns.
When launched, the malware goes via a number of decryption steps earlier than its remaining payload is loaded by way of course of hollowing into an “explorer.exe” course of, working instantly from reminiscence.
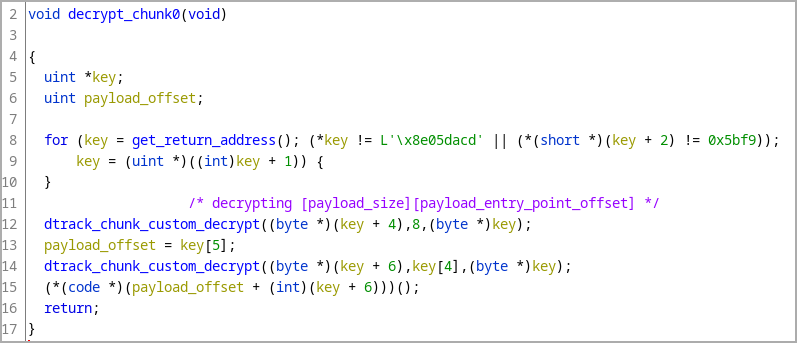
The solely variations to previous DTrack variants are it now makes use of API hashing to load libraries and capabilities as an alternative of obfuscated strings, and that the variety of C2 servers has been minimize by half to simply three.
Some of the C2 servers uncovered by Kaspersky are “pinkgoat[.]com”, “purewatertokyo[.]com”, “purplebear[.]com”, and “salmonrabbit[.]com.”
DTrack attribution
Kaspersky attributes this exercise to the North Korean Lazarus hacking group and claims the menace actors use DTrack each time they see the potential for monetary features.
In August 2022, the identical researchers linked the backdoor to the North Korean hacking group tracked as ‘Andariel,’ which deployed Maui ransomware in company networks within the U.S. and South Korea.
In February 2020, Dragos linked DTrack to a North Korean menace group, ‘Wassonite,’ which attacked nuclear power and oil and fuel services.
