[ad_1]
The core protocol of the Internet, aptly named the
Internet Protocol (IP), defines an addressing scheme that computer systems use to speak with each other. This scheme assigns addresses to particular gadgets—individuals’s computer systems in addition to servers—and makes use of these addresses to ship information between them as wanted.
It’s a mannequin that works nicely for sending distinctive info from one level to a different, say, your financial institution assertion or a letter from a cherished one. This method made sense when the Internet was used primarily to ship completely different content material to completely different individuals. But this design just isn’t nicely suited to the mass consumption of static content material, akin to films or TV reveals.
The actuality right now is that the Internet is extra usually used to ship precisely the identical factor to many individuals, and it’s doing an enormous quantity of that now, a lot of which is within the type of video. The calls for develop even larger as our screens receive ever-increasing resolutions, with 4K video already in widespread use and 8K on the horizon.
The
content material supply networks (CDNs) utilized by streaming companies akin to Netflix assist tackle the issue by briefly storing content material near, and even inside, many ISPs. But this technique depends on ISPs and CDNs with the ability to make offers and deploy the required infrastructure. And it might nonetheless go away the sides of the community having to deal with extra site visitors than truly must movement.
The actual downside just isn’t a lot the amount of content material being handed round—it’s how it’s being delivered, from a central supply to many various far-away customers, even when these customers are situated proper subsequent to at least one one other.
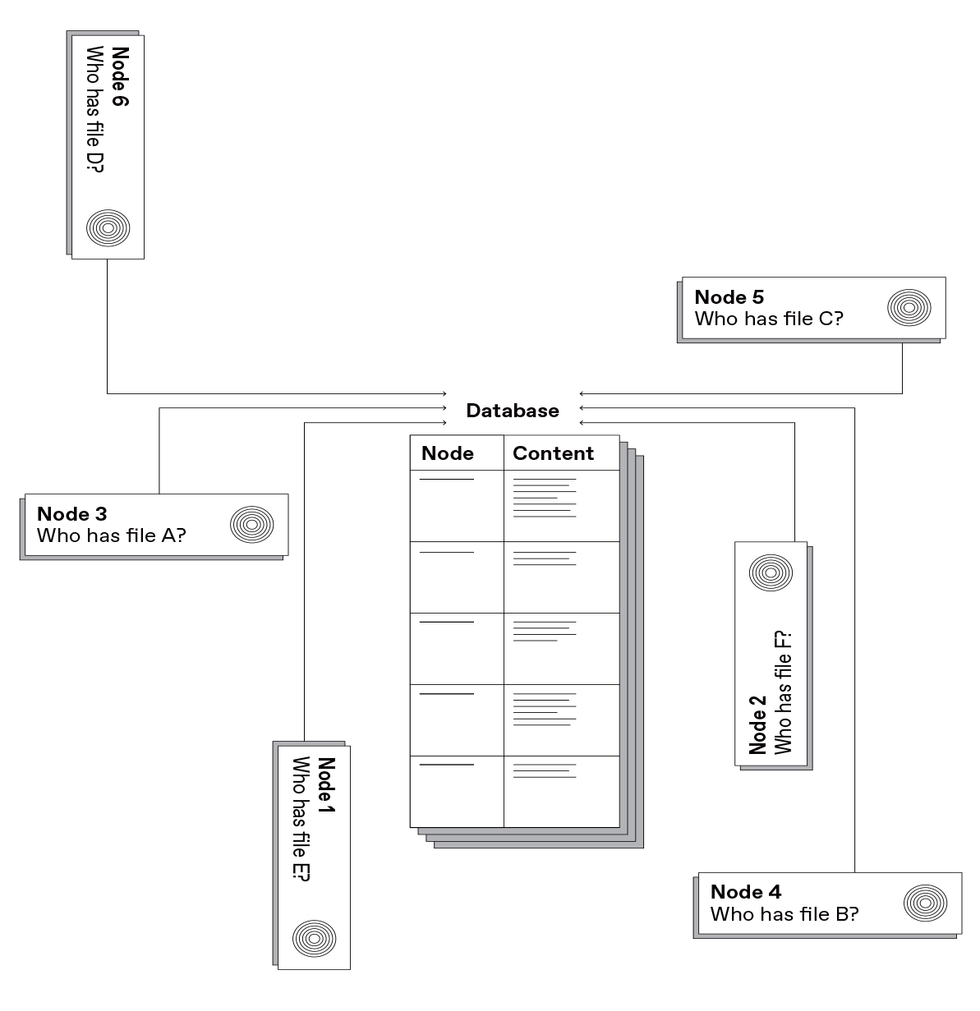 One scheme utilized by peer-to-peer programs to find out the situation of a file is to maintain that info in a centralized database. Napster, the primary large-scale peer-to-peer content-delivery system, used this method.Carl De Torres
One scheme utilized by peer-to-peer programs to find out the situation of a file is to maintain that info in a centralized database. Napster, the primary large-scale peer-to-peer content-delivery system, used this method.Carl De Torres
A extra environment friendly distribution scheme in that case could be for the info to be served to your machine out of your neighbor’s machine in a direct peer-to-peer method. But how would your machine even know whom to ask? Welcome to the InterPlanetary File System (IPFS).
The InterPlanetary File System will get its identify as a result of, in idea, it may very well be prolonged to share information even between computer systems on completely different planets of the photo voltaic system. For now, although, we’re centered on rolling it out for simply Earth!
The key to IPFS is what’s known as content material addressing. Instead of asking a selected supplier, “Please send me this file,” your machine asks the community, “Who can send me this file?” It begins by querying friends: different computer systems within the person’s neighborhood, others in the identical home or workplace, others in the identical neighborhood, others in the identical metropolis—increasing progressively outward to globally distant places, if want be, till the system finds a duplicate of what you’re in search of.
These queries are made utilizing IPFS, a substitute for the
Hypertext Transfer Protocol (HTTP), which powers the World Wide Web. Building on the ideas of peer-to-peer networking and content-based addressing, IPFS permits for a decentralized and distributed community for information storage and supply.
The advantages of IPFS embrace quicker and more-efficient distribution of content material. But they don’t cease there. IPFS also can enhance safety with content-integrity checking in order that information can’t be tampered with by middleman actors. And with IPFS, the community can proceed working even when the connection to the originating server is lower or if the service that originally supplied the content material is experiencing an outage—significantly vital in locations with networks that work solely intermittently. IPFS additionally provides resistance to censorship.
To perceive extra totally how IPFS differs from most of what takes place on-line right now, let’s take a fast have a look at the Internet’s structure and a few earlier peer-to-peer approaches.
As talked about above, with right now’s Internet structure, you request content material primarily based on a server’s tackle. This comes from the protocol that underlies the Internet and governs how information flows from level to level, a scheme first described by Vint Cerf and Bob Kahn in a 1974 paper within the IEEE Transactions on Communications and now often known as the Internet Protocol. The World Wide Web is constructed on prime of the Internet Protocol. Browsing the Web consists of asking a particular machine, recognized by an IP tackle, for a given piece of information.
Instead of asking a selected supplier, “Please send me this file,” your machine asks the community, “Who can send me this file?”
The course of begins when a person varieties a URL into the tackle bar of the browser, which takes the hostname portion and sends it to a
Domain Name System (DNS) server. That DNS server returns a corresponding numerical IP tackle. The person’s browser will then connect with the IP tackle and ask for the Web web page situated at that URL.
In different phrases, even when a pc in the identical constructing has a duplicate of the specified information, it’s going to neither see the request, nor would it not be capable of match it to the copy it holds as a result of the content material doesn’t have an intrinsic identifier—it isn’t content-addressed.
A content-addressing mannequin for the Internet would give information, not gadgets, the main function. Requesters would ask for the content material explicitly, utilizing a singular identifier (akin to the
DOI quantity of a journal article or the ISBN of a e book), and the Internet would deal with forwarding the request to an out there peer that has a duplicate.
The main problem in doing so is that it will require adjustments to the core Internet infrastructure, which is owned and operated by hundreds of ISPs worldwide, with no central authority capable of management what all of them do. While this distributed structure is among the Internet’s biggest strengths, it makes it almost unattainable to make elementary adjustments to the system, which might then break issues for most of the individuals utilizing it. It’s usually very exhausting even to implement incremental enhancements. instance of the problem encountered when introducing change is
IPv6, which expands the variety of attainable IP addresses. Today, virtually 25 years after its introduction, it nonetheless hasn’t reached 50 % adoption.
A means round this inertia is to implement adjustments at a better layer of abstraction, on prime of current Internet protocols, requiring no modification to the underlying networking software program stacks or intermediate gadgets.
Other peer-to-peer programs apart from IPFS, akin to
BitTorrent and Freenet, have tried to do that by introducing programs that may function in parallel with the World Wide Web, albeit usually with Web interfaces. For instance, you may click on on a Web hyperlink for the BitTorrent tracker related to a file, however this course of usually requires that the tracker information be handed off to a separate software out of your Web browser to deal with the transfers. And if you happen to can’t discover a tracker hyperlink, you may’t discover the info.
Freenet additionally makes use of a distributed peer-to-peer system to retailer content material, which may be requested by way of an identifier and may even be accessed utilizing the Web’s HTTP protocol. But Freenet and IPFS have completely different goals: Freenet has a robust concentrate on anonymity and manages the replication of information in ways in which serve that aim however reduce efficiency and person management. IPFS gives versatile, high-performance sharing and retrieval mechanisms however retains management over information within the arms of the customers.
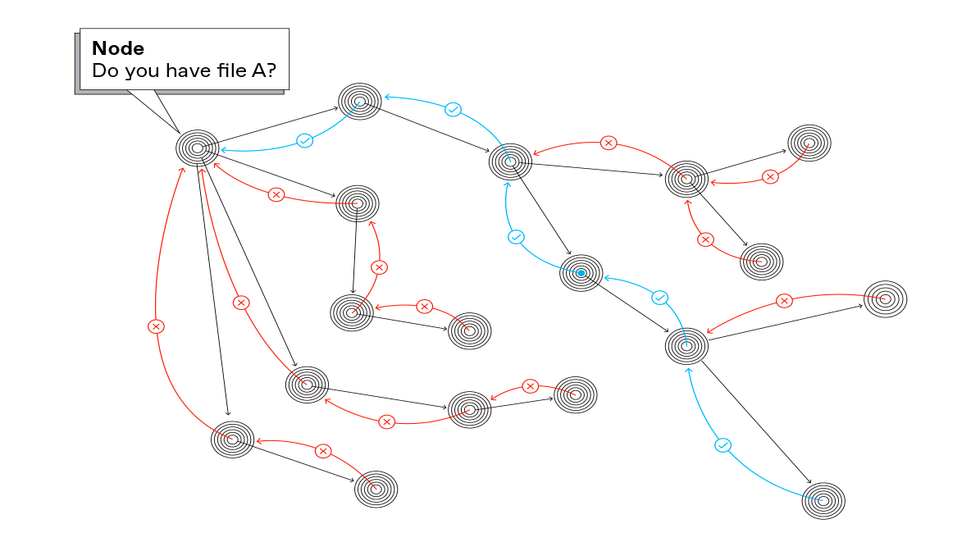 Another method to discovering a file in a peer-to-peer community known as question flooding. The node in search of a file broadcasts a request for it to all nodes to which it’s connected. If the node receiving the request doesn’t have the file [red], it forwards the request to all of the nodes to which it’s connected till lastly a node with the file passes a duplicate again to the requester [blue]. The Gnutella peer-to-peer community used this protocol.Carl De Torres
Another method to discovering a file in a peer-to-peer community known as question flooding. The node in search of a file broadcasts a request for it to all nodes to which it’s connected. If the node receiving the request doesn’t have the file [red], it forwards the request to all of the nodes to which it’s connected till lastly a node with the file passes a duplicate again to the requester [blue]. The Gnutella peer-to-peer community used this protocol.Carl De Torres
We designed IPFS as a protocol to improve the Web and to not create another model. It is designed to make the Web higher, to permit individuals to work offline, to make hyperlinks everlasting, to be quicker and safer, and to make it as straightforward as attainable to make use of.
IPFS began in 2013 as an open-source challenge supported by Protocol Labs, the place we work, and constructed by a vibrant group and ecosystem with a whole lot of organizations and hundreds of builders. IPFS is constructed on a robust basis of earlier work in peer-to-peer (P2P) networking and content-based addressing.
The core tenet of all P2P programs is that customers concurrently take part as purchasers (which request and obtain recordsdata from others)
and as servers (which retailer and ship recordsdata to others). The mixture of content material addressing and P2P gives the suitable substances for fetching information from the closest peer that holds a duplicate of what’s desired—or extra appropriately, the closest one when it comes to community topology, although not essentially in bodily distance.
To make this occur, IPFS produces a fingerprint of the content material it holds (known as a
hash) that no different merchandise can have. That hash may be considered a singular tackle for that piece of content material. Changing a single bit in that content material will yield a completely completely different tackle. Computers desirous to fetch this piece of content material broadcast a request for a file with this specific hash.
Because identifiers are distinctive and by no means change, individuals usually consult with IPFS because the “Permanent Web.” And with identifiers that by no means change, the community will be capable of discover a particular file so long as some pc on the community shops it.
Name persistence and immutability inherently present one other important property: verifiability. Having the content material and its identifier, a person can confirm that what was acquired is what was requested for and has not been tampered with, both in transit or by the supplier. This not solely improves safety but additionally helps safeguard the general public document and stop historical past from being rewritten.
You would possibly surprise what would occur with content material that must be up to date to incorporate recent info, akin to a Web web page. This is a legitimate concern and IPFS does have a set of mechanisms that might level customers to essentially the most up-to-date content material.
Reducing the duplication of information shifting via the community and procuring it from close by sources will let ISPs present quicker service at decrease value.
The world had an opportunity to look at how content material addressing labored in April 2017 when the federal government of Turkey
blocked entry to Wikipedia as a result of an article on the platform described Turkey as a state that sponsored terrorism. Within every week, a full copy of the Turkish model of Wikipedia was added to IPFS, and it remained accessible to individuals within the nation for the almost three years that the ban continued.
An analogous demonstration occurred half a yr later, when the Spanish authorities tried to suppress an independence referendum in Catalonia, ordering ISPs to dam associated web sites. Once once more, the data
remained out there by way of IPFS.
IPFS is an open, permissionless community: Any person can be part of and fetch or present content material. Despite quite a few open-source success tales, the present Internet is closely primarily based on closed platforms, a lot of which undertake lock-in ways but additionally provide customers nice comfort. While IPFS can present improved effectivity, privateness, and safety, giving this decentralized platform the extent of usability that individuals are accustomed to stays a problem.
You see, the peer-to-peer, unstructured nature of IPFS is each a power and a weak point. While CDNs have constructed sprawling infrastructure and superior strategies to supply high-quality service, IPFS nodes are operated by finish customers. The community subsequently depends on their conduct—how lengthy their computer systems are on-line, how good their connectivity is, and what information they determine to cache. And usually these issues aren’t optimum.
One of the important thing analysis questions for the oldsters working at Protocol Labs is find out how to hold the IPFS community resilient regardless of shortcomings within the nodes that make it up—and even when these nodes exhibit egocentric or malicious conduct. We’ll want to beat such points if we’re to maintain the efficiency of IPFS aggressive with standard distribution channels.
You might have observed that we haven’t but supplied an instance of an IPFS tackle. That’s as a result of hash-based addressing ends in URLs that aren’t straightforward to spell out or kind.
For occasion, yow will discover the Wikipedia emblem on IPFS through the use of the next tackle in an appropriate browser:
ipfs://QmRW3V9znzFW9M5FYbitSEvd5dQrPWGvPvgQD6LM22Tv8D/. That lengthy string may be considered a digital fingerprint for the file holding that emblem.
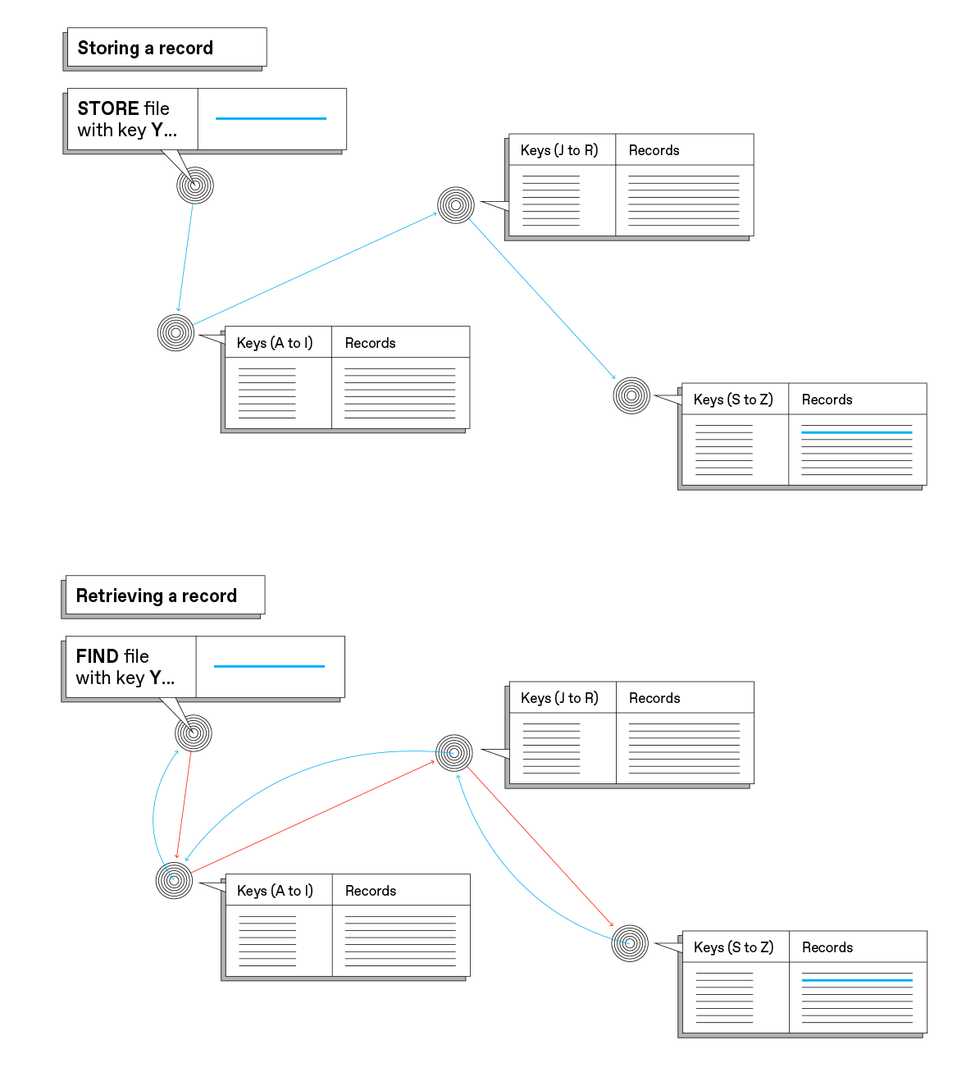 To hold monitor of which nodes maintain which recordsdata, the InterPlanetary File System makes use of what’s known as a distributed hash desk. In this simplified view, three nodes maintain completely different elements of a desk that has two columns: One column (Keys) incorporates hashes of the saved recordsdata; the opposite column (Records) incorporates the recordsdata themselves. Depending on what its hashed secret’s, a file will get saved within the acceptable place [left]—depicted right here as if the system checked the primary letter of hashes and saved completely different elements of the alphabet in other places. The precise algorithm for distributing recordsdata is extra complicated, however the idea is comparable. Retrieving a file is environment friendly as a result of it’s attainable to find the file in line with what its hash is [right].Carl De Torres
To hold monitor of which nodes maintain which recordsdata, the InterPlanetary File System makes use of what’s known as a distributed hash desk. In this simplified view, three nodes maintain completely different elements of a desk that has two columns: One column (Keys) incorporates hashes of the saved recordsdata; the opposite column (Records) incorporates the recordsdata themselves. Depending on what its hashed secret’s, a file will get saved within the acceptable place [left]—depicted right here as if the system checked the primary letter of hashes and saved completely different elements of the alphabet in other places. The precise algorithm for distributing recordsdata is extra complicated, however the idea is comparable. Retrieving a file is environment friendly as a result of it’s attainable to find the file in line with what its hash is [right].Carl De Torres
There are different content-addressing schemes that use human-readable naming, or hierarchical, URL-style naming, however every comes with its personal set of trade-offs. Finding sensible methods to make use of human-readable names with IPFS would go a great distance towards bettering user-friendliness. It’s a aim, however we’re not there but.
Protocol Labs, has been tackling these and different technical, usability, and societal points for many of the final decade. Over this time, we now have been seeing quickly rising adoption of IPFS, with its community dimension doubling yr over yr. Scaling up at such speeds brings many challenges. But that’s par for the course when your intent is altering the Internet as we all know it.
Widespread adoption of content material addressing and IPFS ought to assist the entire Internet ecosystem. By empowering customers to request actual content material and confirm that they acquired it unaltered, IPFS will enhance belief and safety. Reducing the duplication of information shifting via the community and procuring it from close by sources will let ISPs present quicker service at decrease value. Enabling the community to proceed offering service even when it turns into partitioned will make our infrastructure extra resilient to pure disasters and different large-scale disruptions.
But is there a darkish aspect to decentralization? We usually hear issues about how peer-to-peer networks could also be utilized by unhealthy actors to help criminality. These issues are vital however generally overstated.
One space the place IPFS improves on HTTP is in permitting complete auditing of saved information. For instance, due to its content-addressing performance and, particularly, to using distinctive and everlasting content material identifiers, IPFS makes it simpler to find out whether or not sure content material is current on the community, and which nodes are storing it. Moreover, IPFS makes it trivial for customers to determine what content material they distribute and what content material they cease distributing (by merely deleting it from their machines).
At the identical time, IPFS gives no mechanisms to permit for censorship, provided that it operates as a distributed P2P file system with no central authority. So there is no such thing as a actor with the technical means to ban the storage and propagation of a file or to delete a file from different friends’ storage. Consequently, censorship of undesirable content material can’t be technically enforced, which represents a safeguard for customers whose freedom of speech is beneath risk. Lawful requests to take down content material are nonetheless attainable, however they should be addressed to the customers truly storing it, avoiding commonplace abuses (like illegitimate
DMCA takedown requests) in opposition to which giant platforms have difficulties defending.
Ultimately, IPFS is an open community, ruled by group guidelines, and open to everybody. And you may grow to be part of it right now! The
Brave browser ships with built-in IPFS help, as does Opera for Android. There are browser extensions out there for Chrome and Firefox, and IPFS Desktop makes it straightforward to run an area node. Several organizations present IPFS-based internet hosting companies, whereas others function public gateways that can help you fetch information from IPFS via the browser with none particular software program.
These gateways act as entries to the P2P community and are vital to bootstrap adoption. Through some easy DNS magic, a site may be configured so {that a} person’s entry request will consequence within the corresponding content material being retrieved and served by a gateway, in a means that’s fully clear to the person.
So far, IPFS has been used to construct diversified purposes, together with programs for
e-commerce, safe distribution of scientific information units, mirroring Wikipedia, creating new social networks, sharing most cancers information, blockchain creation, safe and encrypted personal-file storage and sharing, developerinstruments, and information analytics.
You might have used this community already: If you’ve ever visited the Protocol Labs website (
Protocol.ai), you’ve retrieved pages of a web site from IPFS with out even realizing it!
This article seems within the November 2022 print subject as “To the InterPlanetary File System—and Beyond!”
From Your Site Articles
Related Articles Around the Web
