[ad_1]
A lately found cyber espionage group dubbed Worok has been discovered hiding malware in seemingly innocuous picture recordsdata, corroborating a vital hyperlink within the menace actor’s an infection chain.
Czech cybersecurity agency Avast mentioned the aim of the PNG recordsdata is to hide a payload that is used to facilitate info theft.
“What is noteworthy is information assortment from victims’ machines utilizing DropBox repository, in addition to attackers utilizing DropBox API for communication with the ultimate stage,” the corporate mentioned.
The growth comes a bit over two months after ESET disclosed particulars of assaults carried out by Worok in opposition to high-profile corporations and native governments positioned in Asia and Africa. Worok is believed to share tactical overlaps with a Chinese menace actor tracked as TA428.
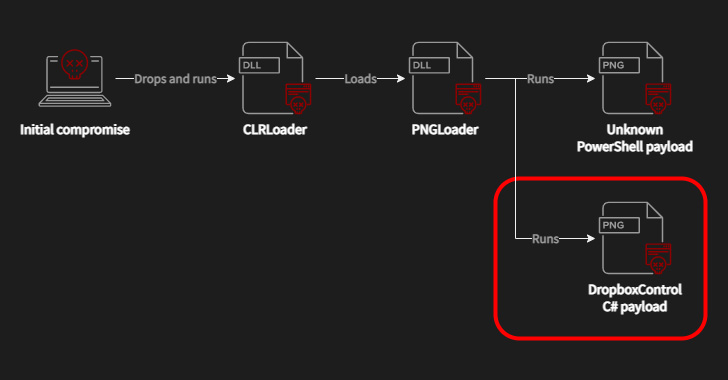
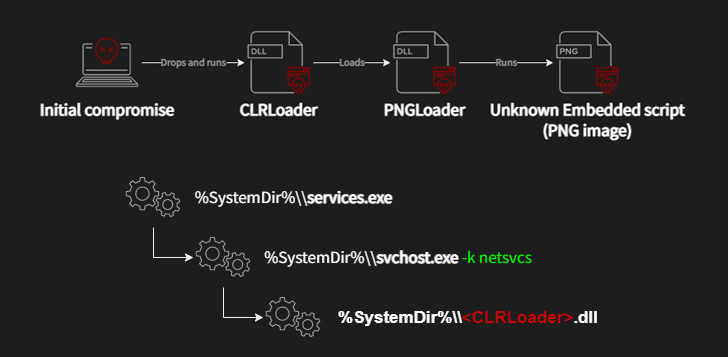
The Slovak cybersecurity firm additionally documented Worok’s compromise sequence, which makes use of a C++-based loader known as CLRLoad to pave the best way for an unknown PowerShell script embedded inside PNG photos, a method often known as steganography.
That mentioned, the preliminary assault vector stays unknown as but, though sure intrusions have entailed the usage of ProxyShell vulnerabilities in Microsoft Exchange Server to deploy the malware.
Avast’s findings present that the adversarial collective makes use of DLL side-loading upon gaining preliminary entry to execute the CLRLoad malware, however not earlier than performing lateral motion throughout the contaminated surroundings.
PNGLoad, which is launched by CLRLoad (or alternatively one other first-stage known as PowHeartBeat), is alleged to return in two variants, every chargeable for decoding the malicious code throughout the picture to launch both a PowerShell script or a .NET C#-based payload.
The PowerShell script has continued to be elusive, though the cybersecurity firm famous it was capable of flag a couple of PNG recordsdata belonging to the second class that allotted a steganographically embedded C# malware.
“At first look, the PNG photos look harmless, like a fluffy cloud,” Avast mentioned. “In this particular case, the PNG recordsdata are positioned in C:Program InformationInternet Explorer, so the image doesn’t appeal to consideration as a result of Internet Explorer has the same theme.”
This new malware, dubbed DropBoxControl, is an information-stealing implant that makes use of a Dropbox account for command-and-control, enabling the menace actor to add and obtain recordsdata to particular folders in addition to run instructions current in a sure file.
Some of the notable instructions embrace the power to execute arbitrary executables, obtain and add information, delete and rename recordsdata, seize file info, sniff community communications, and exfiltrate system metadata.
Companies and authorities establishments in Cambodia, Vietnam, and Mexico are few of the outstanding nations affected by DropBoxControl, Avast mentioned, including the authors of the malware are possible totally different from these behind CLRLoad and PNGLoad owing to “considerably totally different code high quality of those payloads.”
Regardless, the deployment of the third-stage implant as a instrument to reap recordsdata of curiosity clearly signifies the intelligence-gathering goals of Worok, to not point out serves for instance an extension to its killchain.
“The prevalence of Worok’s instruments within the wild is low, so it might point out that the toolset is an APT mission specializing in high-profile entities in non-public and public sectors in Asia, Africa, and North America,” the researchers concluded.