[ad_1]
IT service administration software program platform ConnectWise has launched Software patches for a important safety vulnerability in Recover and R1Soft Server Backup Manager (SBM).
The situation, characterised as a “neutralization of Special Elements in Output Used by a Downstream Component,” may very well be abused to end result within the execution of distant code or disclosure of delicate data.
ConnectWise’s advisory notes that the flaw impacts Recover v2.9.7 and earlier, in addition to R1Soft SBM v6.16.3 and earlier, are impacted by the important flaw.
At its core, the difficulty is tied to an upstream authentication bypass vulnerability within the ZK open supply Ajax net software framework (CVE-2022-36537), which was initially patched in May 2022.
“Affected ConnectWise Recover SBMs have robotically been up to date to the most recent model of Recover (v2.9.9),” the corporate mentioned, urging prospects to improve to SBM v6.16.4 shipped on October 28, 2022.
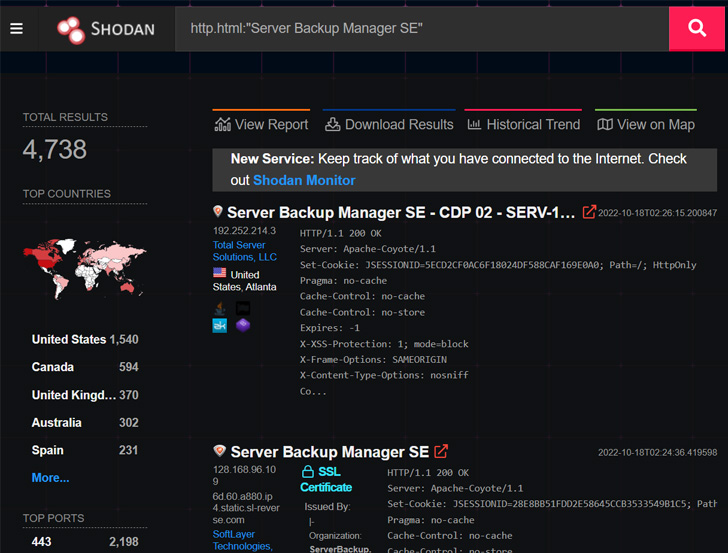
Cybersecurity agency Huntress mentioned it recognized “upwards of 5,000 uncovered server supervisor backup situations,” doubtlessly exposing firms to produce chain dangers.
While there isn’t any proof of lively exploitation of the vulnerability within the wild, a proof-of-concept devised by Huntress researchers John Hammond and Caleb Stewart exhibits that it may be abused to bypass authentication, acquire distant code execution on SBM, and push LockBit 3.0 ransomware to all downstream endpoints.
“It is vital to notice that the upstream ZK vulnerability not solely impacts R1Soft, but in addition any software using an unpatched model of the ZK framework,” the researchers mentioned.
“The entry an attacker can acquire by utilizing this authentication bypass vulnerability is particular to the appliance being exploited, nevertheless there may be critical potential for different functions to be affected in an analogous solution to R1Soft Server Backup Manager.”