[ad_1]
The operators of RomCom RAT malware are persevering with to evolve their campaigns by distributing rogue variations of software program corresponding to SolarWinds Network Performance Monitor, KeePass password supervisor, and PDF Reader Pro through faux copycat web sites.
Targets of the operation include victims in Ukraine and choose English-speaking international locations just like the U.Okay.
“Given the geography of the targets and the present geopolitical scenario, it is unlikely that the RomCom RAT risk actor is cybercrime-motivated,” the BlackBerry Threat Research and Intelligence Team stated in a brand new evaluation.
The newest findings come per week after the Canadian cybersecurity firm disclosed a spear-phishing marketing campaign aimed toward Ukrainian entities to deploy a distant entry trojan known as RomCom RAT.
The unknown risk actor has additionally been noticed leveraging trojanized variants of Advanced IP Scanner and pdfFiller as droppers to distribute the implant.
The newest iteration of the marketing campaign entails organising decoy lookalike web sites with an analogous area title, adopted by importing a malware-laced installer bundle of the malicious software program, after which sending phishing emails to focused victims.
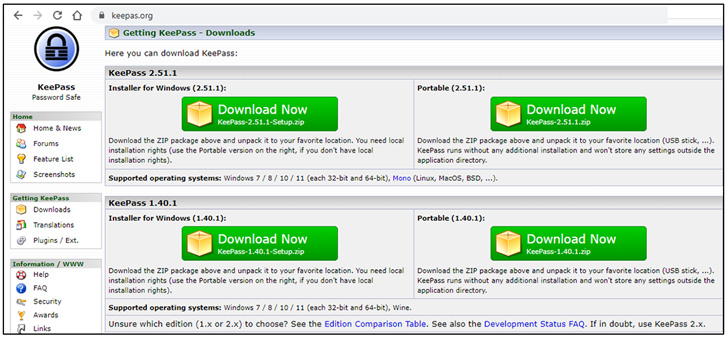 |
| Fake Keypass web site |
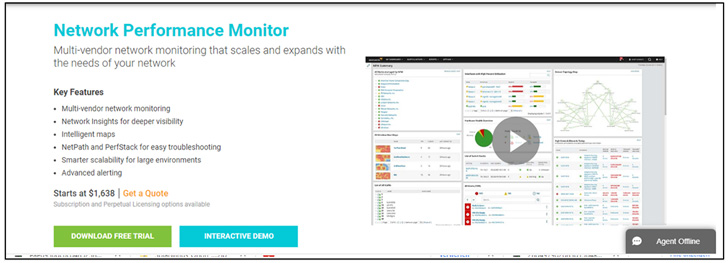 |
| Fake SolarWinds web site |
“While downloading a free trial from the spoofed SolarWinds web site, a professional registration type seems,” the researchers defined.
“If crammed out, actual SolarWinds gross sales personnel would possibly contact the sufferer to comply with up on the product trial. That approach misleads the sufferer into believing that the not too long ago downloaded and put in software is totally professional.”
It’s not simply SolarWinds software program. Other impersonated variations contain the favored password supervisor KeePass and PDF Reader Pro, together with within the Ukrainian language.
The use of RomCom RAT has additionally been linked to risk actors related to the Cuba ransomware and Industrial Spy, based on Palo Alto Networks Unit 42, which is monitoring the the ransomware affiliate underneath the constellation-themed moniker Tropical Scorpius.
Given the interconnected nature of the cybercriminal ecosystem, it is not instantly evident if the 2 units of actions share any connections or if the malware is obtainable on the market as a service to different risk actors.
“The obvious RomCom connection to Cuba Ransomware and Industrial Spy teams relies on the community configuration hyperlink, which could even be used as a distraction,” BlackBerry’s Dmitry Bestuzhev stated. “Given the character of the targets and geographical location of the victims, it is evident the motivation will not be a monetary one.”
Update: Palo Alto Networks Unit 42 stated it additionally uncovered an occasion of RomCom RAT packaged as an installer for the Veeam Backup & Replication software program that is hosted on a malicious area named “wveeam[.]com.”
Like within the case of SolarWinds, downloading the installer file redirects the sufferer to a type that prompts the sufferer to enter their private particulars. What’s extra, the scale of the modified installer is greater than 10GB, permitting it to bypass automated safety options.
“These instruments are usually utilized by Western mid-size organizations,” Pete Renals, principal researcher at Unit 42, advised The Hacker News in an announcement. “Based on Unit 42’s evaluation of RomCom focusing on, infrastructure, and packaging, it means that this marketing campaign is extra broad than an APT focus.”
“As of now, we’ve solely seen RomCom malware utilized by Cuba ransomware,” Doel Santos, senior risk researcher at Unit 42, additional added.


