[ad_1]
Orcus is a Remote Access Trojan with some distinctive traits. The RAT permits attackers to create plugins and presents a strong core characteristic set that makes it fairly a harmful computer virus in its class.
RAT is kind of a steady kind that all the time makes it to the highest.
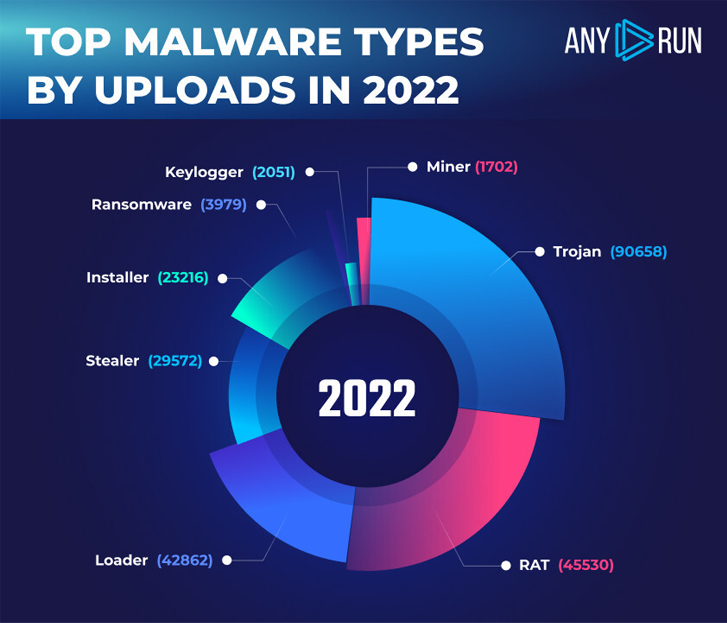 |
| ANY.RUN’s high malware varieties in 2022 |
That’s why you will undoubtedly come throughout this kind in your apply, and the Orcus household particularly. To simplify your evaluation, we now have collected 3 lifehacks you need to reap the benefits of. Here we go.
What is Orcus RAT?
Definition. Orcus RAT is a kind of malicious software program program that allows distant entry and management of computer systems and networks. It is a kind of Remote Access Trojan (RAT) that has been utilized by attackers to realize entry to and management computer systems and networks.
Capabilities. Once downloaded onto a pc or community, it begins to execute its malicious code, permitting the attacker to realize entry and management. It is able to stealing knowledge, conducting surveillance, and launching DDoS assaults.
Distribution. The malware is normally unfold by way of malicious emails, web sites, and social engineering assaults. It can be usually bundled with different malicious software program packages, resembling Trojans, worms, and viruses.
Lifehacks for Orcus RAT malware evaluation
The malware is designed to be tough to detect, because it usually makes use of subtle encryption and obfuscation methods to stop detection. And if you’ll want to get to the core of Orcus, the RAT configuration has all the info you want.
And there are a number of lifehacks that you need to take note of whereas performing the evaluation of Orcus RAT.
Today we examine the .NET pattern that you may obtain at no cost in ANY.RUN database:
SHA-256: 258a75a4dee6287ea6d15ad7b50b35ac478c156f0d8ebfc978c6bbbbc4d441e1
1 — Get to know Orcus lessons
You ought to begin with checking malware lessons the place you may get the hidden program’s traits. A bunch of information that lessons include is precisely what will probably be useful on your analysis.
An Orcus.Config namespace has these lessons:
- Consts: Orcus’s information and directories knowledge, e.g. the trail to the file the place consumer keystrokes are saved or to the listing the place the plugins utilized by a pattern reside.
- Settings: include wrapper strategies for decrypting the malware configuration and its plugins.
- SettingsInformation: is a static class solely with the encrypted malware and plugin configuration fields.
2 — Find Orcus RAT sources
Once you dive into the Settings class, you’ll be able to discover the GetDecryptedSettings methodology. Later, it calls out the AES.Decrypt. And it appears like your job is completed and the malware configuration is lastly discovered. But maintain on – the meeting would not include an Orcus.Shared.Encryption namespace.
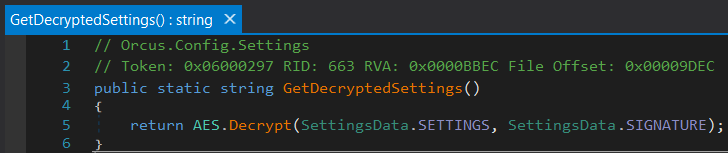 |
| GetDecryptedSettings methodology |
Orcus RAT shops extra assemblies contained in the malware sources utilizing a ‘deflate’ algorithm. You can go to the sources to seek out the required meeting. Unpacking them will allow you to reveal the decryption algorithm that an Orcus pattern makes use of. That brings yet one more lifehack for at this time.
3 — Decrypt knowledge
Our treasure hunt goes on, as configuration knowledge is encrypted.
Orcus RAT encrypts knowledge utilizing the AES algorithm after which encodes the encrypted knowledge utilizing Base64.
How to decrypt knowledge:
- generate the important thing from a given string utilizing Microsoft’s PBKDF1 implementation
- decode the info from Base64
- apply the generated key to decrypt the info by way of the AES256 algorithm in CBC mode.
As a results of decoding, we get the malware configuration within the XML format. And all Orcus secrets and techniques are in your palms now.
Get all of sudden in a malware sandbox
Malware evaluation isn’t a bit of cake, it undoubtedly takes effort and time to crack a pattern. That’s why it is all the time nice to chop the road: get all of sudden and in a short while. The reply is straightforward – use a malware sandbox.
ANY.RUN malware sandbox mechanically retrieves configuration for the Orcus RAT. It’s a a lot simpler approach to analyze a malicious object. Try it now – the service has already retrieved all knowledge from this Orcus pattern, so you’ll be able to get pleasure from easy analysis.
⚡ Write the “hackernews1” promo code at assist@any.run utilizing your small business e mail deal with and get 14 days of ANY.RUN premium subscription at no cost!
Conclusion
The Orcus RAT masquerades as a reliable distant administration software, though it’s clear from its options and performance that it isn’t and was by no means meant to be. Analysis of the malware helps to get info for the cybersecurity of your organization.
Protect your small business from this risk – implement a complete safety technique, prepare staff to acknowledge and keep away from malicious emails and web sites, and use dependable anti-virus and ANY.RUN malware sandbox to detect and analyze Orcus.

