[ad_1]
A high-severity vulnerability has been disclosed within the SQLite database library, which was launched as a part of a code change relationship all the best way again to October 2000 and will allow attackers to crash or management packages.
Tracked as CVE-2022-35737 (CVSS rating: 7.5), the 22-year-old subject impacts SQLite variations 1.0.12 by 3.39.1, and has been addressed in model 3.39.2 launched on July 21, 2022.
“CVE-2022-35737 is exploitable on 64-bit methods, and exploitability is determined by how this system is compiled,” Trail of Bits researcher Andreas Kellas mentioned in a technical write-up printed as we speak.
“Arbitrary code execution is confirmed when the library is compiled with out stack canaries, however unconfirmed when stack canaries are current, and denial-of-service is confirmed in all instances.”
Programmed in C, SQLite is the most generally used database engine, included by default in Android, iOS, Windows, and macOS, in addition to fashionable internet browsers equivalent to Google Chrome, Mozilla Firefox, and Apple Safari.
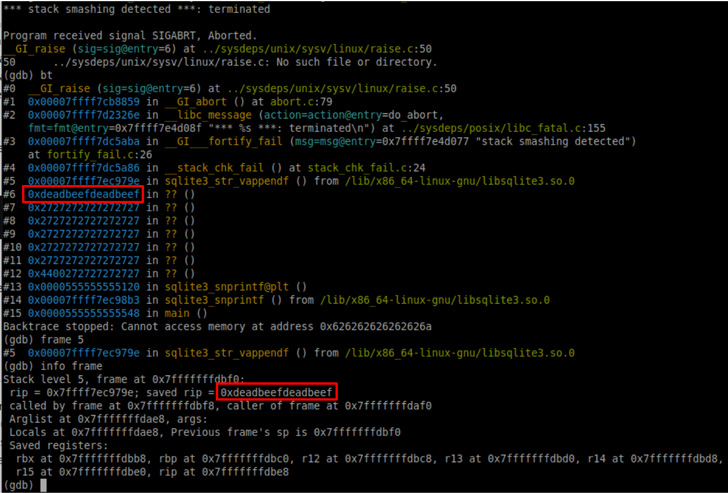
The vulnerability found by Trail of Bits considerations an integer overflow bug that happens when extraordinarily massive string inputs are handed as parameters to the SQLite implementations of the printf capabilities, which, in flip, make use of one other operate to deal with the string formatting (“sqlite3_str_vappendf“).
However, a profitable weaponization of the flaw banks on the prerequisite that the string accommodates the %Q, %q, or %w format substitution varieties, probably resulting in a program crash when user-controlled information is written past the bounds of a stack-allocated buffer.
“If the format string accommodates the ‘!’ particular character to allow unicode character scanning, then it’s doable to realize arbitrary code execution within the worst case, or to trigger this system to hold and loop (practically) indefinitely,” Kellas defined.
The vulnerability can be an instance of a situation that was as soon as deemed impractical many years in the past — allocating 1GB strings as enter — rendered possible with the arrival of 64-bit computing methods.
“It’s a bug that won’t have appeared like an error on the time that it was written (relationship again to 2000 within the SQLite supply code) when methods have been primarily 32-bit architectures,” Kellas mentioned.